Which Email Service Gives Users Most Privacy Security Stack Exchance
Mimecast and Proofpoint customers might be susceptible to email attacks that other Office 365 and Gmail customers are not. Mimecast and Proofpoint were the premier email security solutions for legacy on-premises email platforms, such as Exchange or Lotus Notes. Merely using them for deject-based Office 365 or Gmail actually blinds Microsoft and Google's default security. In some cases, yous are better off without these email gateways. (In "SaaS Electronic mail Security: 7 Reasons non to Apply an MTA Gateway," we summarize why an email gateway is not the right solution for cloud email.) Introducing an MTA (a Mail Transfer Agent that changes your MX tape) will blind Microsoft and Google's default security to incoming threats. As a security visitor, nosotros observe many phishing attacks. Amid these, ane of the most persistent threats is also the most ironic: deploying a secure email gateway from Mimecast or Proofpoint allows emails that would have been blocked by Office 365 or Gmail to bypass all security. This boils down to spending money on a security solution that actually worsens your security posture. When you double-stack your security with a secure email gateway, you lot must disable Microsoft and Google's spam filters — which play a central function in anti-phishing. This is why upon deployment, y'all volition oft be brash by Proofpoint or Mimecast to disable your default spam filtering and rely solely on the gateway. Installing a secure gateway makes emails bypass the native security of your cloud-based email provider. Email security solutions like Mimecast and Proofpoint change certain indicators in the email's header, blinding some critical aspects of the default security layers in Office 365 and Gmail. This would not be a problem if the MTA caught 100% of attacks, but this is not e'er the case, especially in the first hours or days of an event. From a 'defence-in-depth' perspective, information technology is disheartening to know that in order to deploy a 2d layer of security, you must essentially disable the beginning. After the email passes through the gateway, Google and Office 365 tin can no longer interpret two primary indicators of phishing because: 1. The sender'south IP address is changed After Mimecast or Proofpoint is configured, O365 and Gmail no longer see the IP address, which identifies the original sending server of the e-mail. Every bit an email passes through the secure email gateway, it replaces the sender's IP with its own IP address. The following information also becomes unavailable, making the related security dysfunctional: When all mail going through the gateway is "from" the gateway, identifying threats becomes more hard. 2. Sender Policy Framework (SPF) fails Email providers preclude sender address forgery using SPF, a DNS-based security protocol/mechanism, by verifying the sender's IP accost against the sender's domain. With this in mind, imagine y'all've deployed a secure email gateway atop the default security stack of your deject email. In the aforementioned mean solar day, the deject email server receives a legitimate and spoofed e-mail from Banking concern of America. For both emails, SPF has failed because your email provider sees the secure email gateway's IP is not immune to ship on behalf of the sender'southward domain. Considering of this effect, Proofpoint and Mimecast tell you lot to disable the spam and phishing filtering of your e-mail service. Although SPF is not fail-proof, it remains an important indicator for the genuineness of the email. A month ago, we reported on an attack that was bypassing both Microsoft's default security equally well every bit Advanced Threat Protection. Somewhen, Microsoft learned to detect this particular threat, and we stopped seeing the malicious letters. Almost. We continued to come across (and cake) these malicious messages on a scattering of customers. For about a week, our engineers could not understand why only these accounts were affected. Eventually, we discovered what these customers had in mutual: all of them had an MTA email security product deployed. Somehow, the malicious mail was getting by the MTA gateway, merelyalso bypassing Microsoft's ain security — which we knew should accept been able to block it. Microsoft's born security misses this threat considering in lodge to deploy any MTA E-mail Gateway similar Mimecast or Proofpoint, the client must commencement disable Function 365'southward own built-in security. Why? One of the near basic electronic mail checks is the SPF and DKIM authentication of the sending SMTP server. This validates that an email from "visitor.com" truly came from "company.com". However, when you change your MX record and ship information technology through an MTA gateway, every e-mail is sent from the MTA IP address (every bit we discussed higher up) and fails both of these fundamental checks. And then, in order to prevent Microsoft from rejecting every electronic mail sent past the MTA gateway, you must put the Mimecast and Proofpoint servers on a list of "Trusted Servers". "To ensure emails are delivered from Mimecast to Office 365, the Mimecast service IP Ranges should be added to the Allowed List in the Connection Filtering Policy within the Function 365 Exchange Admin Eye (EAC)." -Mimecast Deployment Instructions Unfortunately, this "Allowed List" send rule effectively by-passes Microsoft's own protection. You can see this in the header of every electronic mail that uses an MTA (meet Microsoft Bulletin Headers). So, from Function 365's perspective, this IP address that belongs to Mimecast is marked as a trusted sender for every email. Therefore, every email will featherbed Microsoft's filters and be delivered to the user'southward inbox. If the MTA misses a malicious email, Microsoft's own security will never never see it. Secure e-mail gateways deploy outside of deject email to browse inbound and (for an actress price) outbound threats. By default, Mimecast and Proofpoint don't browse internal email, just they offering information technology — just not in existent-time. Recently, they have introduced a separate product for internal email. Secure email gateways rely on a Rube Goldberg-ian system of tools to quarantine malicious e-mail after they've reached the inbox and have been opened by the victim. Equally you lot can come across in Proofpoint's infographic beneath, these systems: Some of these systems advertise the ability to track downwards forwarded emails, which merely emphasizes the weakness of the machinery; by the time they notice the threat, it's already been read, clicked, and forwarded. Essentially, this is a separate procedure for scanning internal email. No thing how effective their scanning is, this architecture volition never catch threats in real-time. Avanan is uniquely positioned to measure the effectiveness of Microsoft'due south email security. Because we connect via API, we are able to scan email in the line of email traffic — after it has been scanned by Microsoft, butbefore it arrives in the inbox. T his is true across all of our customers — regardless of if they employ only Microsoft'south default security, Accelerate Threat Protection (ATP), or Mimecast and Proofpoint. This allows the states to compare the effectiveness of each email provider's security during big phishing or malware outbreaks. Avanan'southward anti-phishing solution is different than Proofpoint and Mimecast in a few key ways: Because Avanan is deployed internally, nosotros are uniquely positioned inside of deject electronic mail. We scan internal threats with no boosted, cumbersome configuration, equally is the case with gateways. Deploying from inside cloud-based email creates an architectural reward. Rather than replacing one security layer with another (equally you would accept to with Proofpoint or Mimecast), Avanan is some other security layer added to the default security in the platform. Working via API, we scan emails later on they pass through Microsoft'southward filters, but before they achieve the inbox — focusing specifically on what they miss. Because we connect directly to Microsoft's back end, nosotros tin analyze and block a malicious electronic mail before it gets to the user'due south inbox. Deploying via API gives Avanan 100% visibility and more avant-garde enforcement. Because we are working inside Microsoft's infrastructure, nosotros can monitor inbound, outbound, and internal email that would normally be missed by an external email gateway. In fact, we can get dorsum in fourth dimension and search the company's inbox for past attacks, identifying compromised accounts. More importantly, we can attain into a user'due south inbox and quarantine emails that are discovered to be malicious afterward they are delivered. (For case, when it was discovered that an internal account had been compromised, nosotros were able to quarantine every previous email sent past that account across the enterprise. Secure email gateways require that you modify your DNS MX record to point to the security provider instead of your deject e-mail provider. The effect of this setup is that any hacker can know what security service you lot have selected and reverse engineer information technology in a replicated environment to eventually send y'all malware that they know can bypass your security measures. On the other paw, API-based solutions do not expose the security you chose. Yous can add as many security tools on our platform as you choose—all scanning in parallel all emails, all invisible to potential hackers. And then, to be articulate: this is not almost Mimecast or Proofpoint missing a detail email. All security tools miss some. What we are demonstrating is that replacing i security (Microsoft) with another (Mimecast or Proofpoint) might fail you in many cases. The best approach is to work with what Microsoft gives you in the E3 license, and add a tertiary-party vendor who has tighter integration with the Office suite than Proofpoint and Mimecast. We turned to 1 of our customers, a CIO at an Information technology direction company of 3,000 employees who would prefer to remain anonymous. He said, "Avanan defenseless 162 phishing attacks during our 2-week trial, compared to Mimecast and Proofpoint, which caught 101 and 69, respectively. It even had a better faux positive rate." Mimecast and Proofpoint Blind Born Security for Office 365
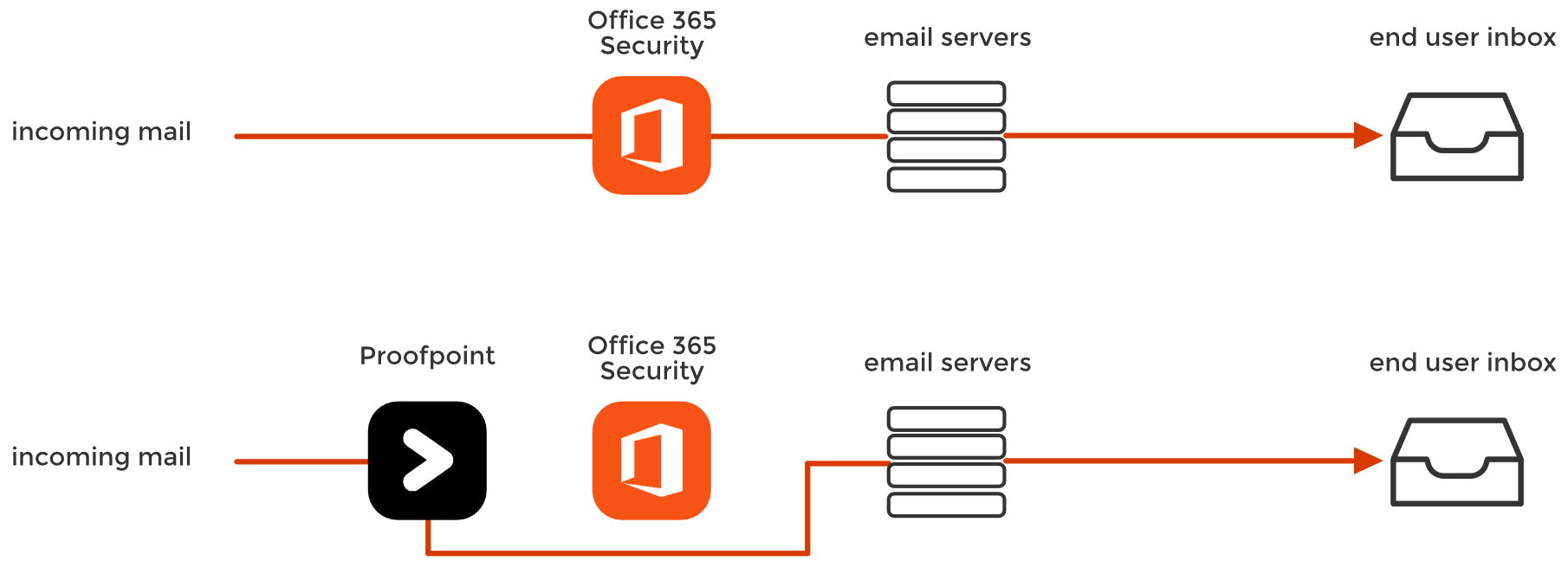
Why Exercise Proofpoint and Mimecast Interfere with Microsoft?
How Hackers Take Advantage of Gateways
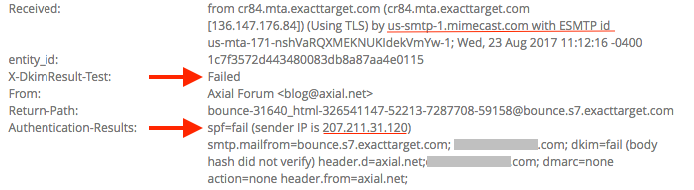
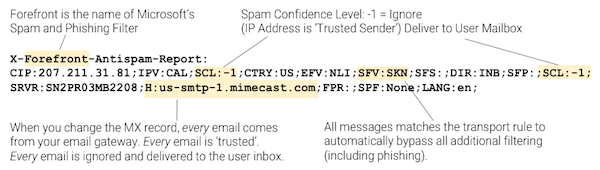
Mimecast and Proofpoint Don't Terminate Internal Threats in Existent-Time
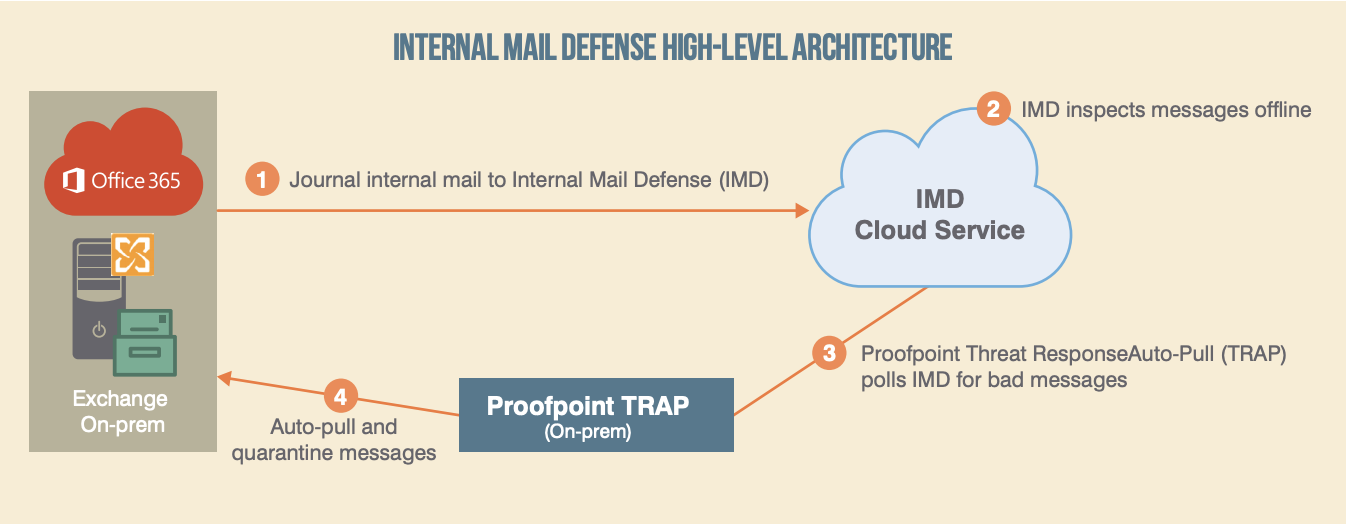
Why Securing Email from inside The Cloud Is Important
1. It Enables I-Click Deployment
.png?width=1000&name=MTA-graphic%20(1).png)
Hackers Tin't See What Security You're Using
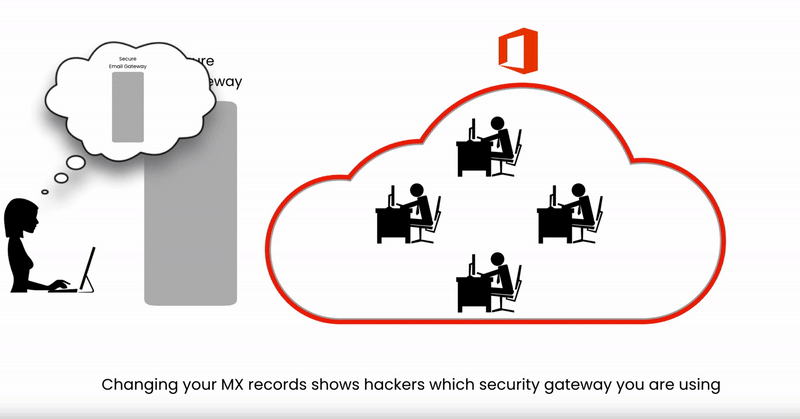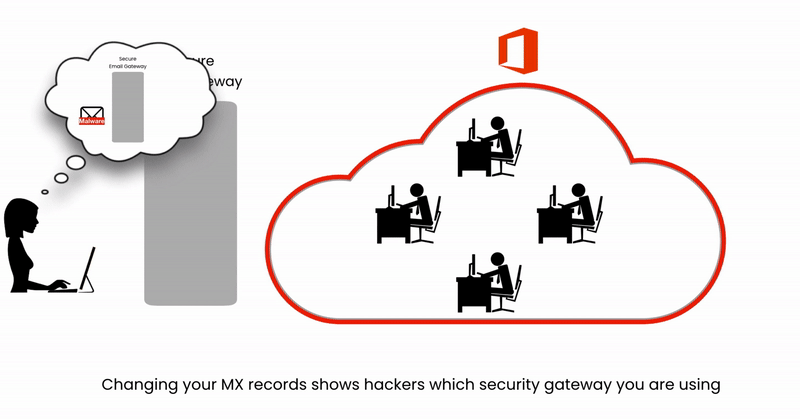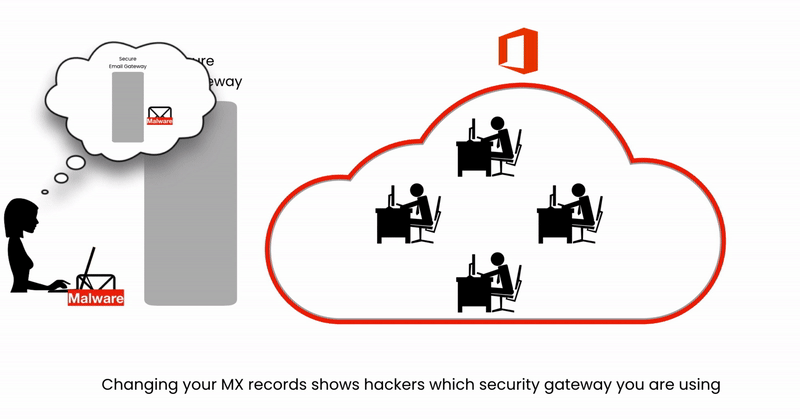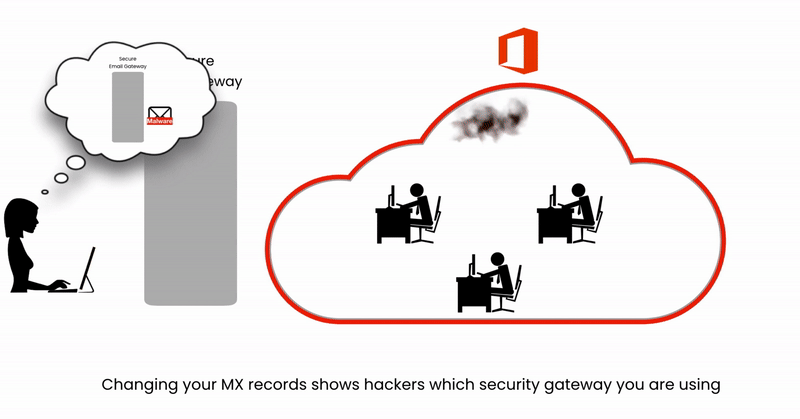
Email Security Is nearly Grab Rate
Which Email Service Gives Users Most Privacy Security Stack Exchance,
Source: https://www.avanan.com/blog/why-proofpoint-and-mimecast-cant-secure-office-365-and-gmail
Posted by: williamsletly1959.blogspot.com


0 Response to "Which Email Service Gives Users Most Privacy Security Stack Exchance"
Post a Comment